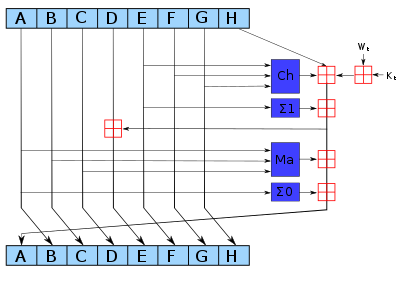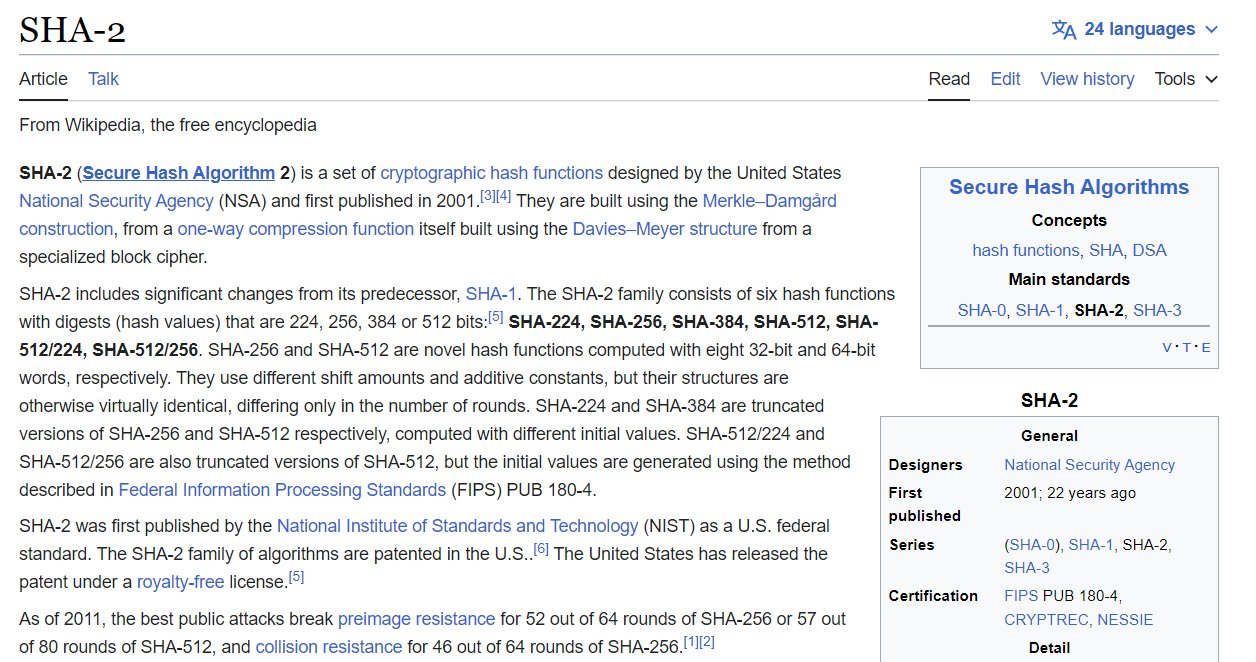
CR1337 on X: "The roots of cryptocurrencies; older than most people think. For example let's take this research essay by NSA employees from 1997: 'How to make a mint: The cryptography of

Why the NSA abandoned the SHA-2 hashing algorithm technology and why Satoshi modified it to create Bitcoin?